20. Two-Factor Authentication
20.1. What is Two-Factor Authentication?
Two-Factor Authentication offers an additional layer of protection used to authenticate users in a more secure manner. DynFi Manager uses the most popular TOTP Time-based one-time password approach. It consists of two steps:
Verification of login/password (basic step, the default one),
Verification of a time-based one-time password generated by an application.
The application (usually a mobile one) generates a new one-time password every 30 seconds. User provides the code in DynFi Manager, which accepts given code only during this 30 seconds range.
20.2. Setting up 2FA TOTP
To set up Two-Factor Authentication go to MyAccount edit page (use the icon on the top-left, then click Edit Account).
Follow instructions provided on the Edit Account page.
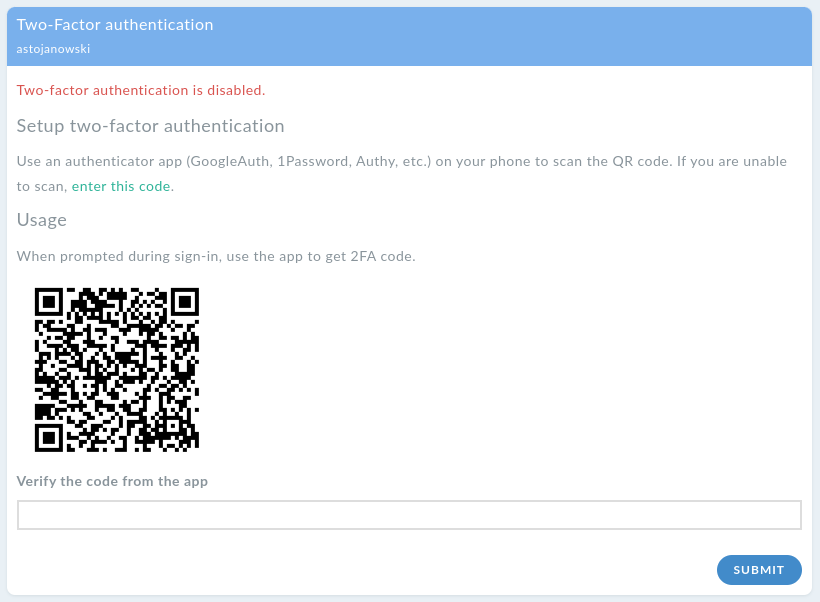
You have to install an application to generate a one-time passwords. DynFi Manager doesn’t force the usage of any particular one. Some of the most popular ones are Google Authenticator, Microsoft Authenticator, LastPass Authenticator or Authy.
Name |
Plateforme |
URL |
|---|---|---|
FreeOTP (recommended) |
Android, iOS |
|
Google Authenticator |
Android, iOS |
|
ID.me Authenticator |
Android, iOS |
https://apps.apple.com/us/app/id-me-authenticator/id1446335066 |
Note
we recommend the usage of FreeOTP because it is an Open Source application developped by RedHat.
Using your selected application, scan the QR-code presented by DynFi Manager (or enter a code if you are unable to scan It), then provide the first code generated by the app. Next time you log in, you will need to provide your password and another OTP generated code using your application.
Note
if you can’t see a section with QR-code displayed on “Edit Account” page, it’s probably caused by missing permissions. Ask the administrator to enable Two-Factor Authentication for your role.
20.3. Forcing Two-Factor Authentication for other users
The Administrator (or any user with “Force two-factor auth” permission enabled) can force another user to enable Two-Factor Authentication.
It can be done using the Edit Account page of any given user or during account creation, see Managing users in DFM.
Once forced, Two-Factor Authentication cannot be bypassed by the user, unless certain permissions have been granted. Administrator can always disable Two-Factor Authentication for any account (including it’s own account).
20.4. Two-Factor Authentication permissions
See Managing users in DFM section to learn how to manage roles and permissions.
“Force two-factor auth” - allows forcing Two-Factor Authentication for other users; recommended for Admin users only,
“Setup own two-factor auth” - allows setting up this authentication method; recommended default,
“Disable own two-factor auth” - if enabled, given user can disable It’s own Two-Factory Authentication; denying this permissions makes it impossible to bypass forced Two-Factor Authentication setup,
“Disable two-factor auth” - if enabled, given user can disable Two-Factory Authentication for other users; recommended for Admin users only.
20.5. Disabling Two-Factor Authentication using CLI
This option might be useful to reset Two-Factor Authentication of an Admin account, if there are no other Administrators.
Please run the following command:
java -jar /path/to/dynfi-version.jar disable2FA --user username [--config /path/to/custom/dynfi.config]
Using the –user parameter the “user’s unique login” or “e-mail address” is required. Additionally, path to custom config file can be provided (if the default file is meant to be skipped) using –config parameter.